(Replacing message template with parser tag) |
(Updated Edited template to July 12, 2025.) |
||
| (One intermediate revision by one other user not shown) | |||
| Line 12: | Line 12: | ||
Then App Registrations, New Application registration: | Then App Registrations, New Application registration: | ||
[[File:2018-05-28 13h27 18.png|none|thumb|828x828px]] | [[File:2018-05-28 13h27 18.png|none|thumb|828x828px]] | ||
Enter a name for your application (just an easy-read identifier) | Enter a name for your application (just an easy-read identifier). | ||
Also enter the sign on URL to your Turnkey – in my case: https://hkscratch.azurewebsites.net/Account/Login | Also enter the sign-on URL to your Turnkey – in my case: https://hkscratch.azurewebsites.net/Account/Login | ||
[[File:2018-05-28 13h28 39.png|none|thumb|704x704px]] | [[File:2018-05-28 13h28 39.png|none|thumb|704x704px]] | ||
You will get this screen with important information: | You will get this screen with important information: | ||
| Line 22: | Line 22: | ||
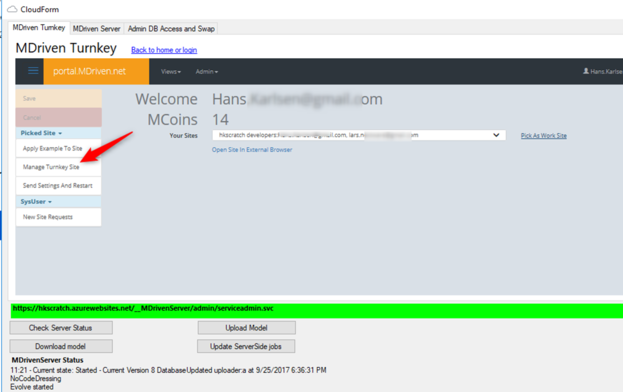
You now have the Application ID Guid and the Authority name. We will now assign these to your application via the Turnkey-portal: | You now have the Application ID Guid and the Authority name. We will now assign these to your application via the Turnkey-portal: | ||
[[File:2018-05-28 13h31 45.png|none|thumb|623x623px]] | [[File:2018-05-28 13h31 45.png|none|thumb|623x623px]] | ||
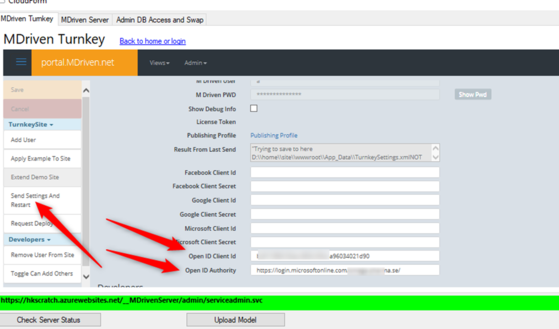
Paste your values in – then Send Settings And Restart: | Paste your values in – then click on Send Settings And Restart: | ||
[[File:2018-05-28 13h33 02.png|none|thumb|559x559px]] | [[File:2018-05-28 13h33 02.png|none|thumb|559x559px]] | ||
The value for OpenId-authority for AzureAD has the form of ''<nowiki>https://login.microsoftonline.com/</nowiki><your authority>/'' | The value for OpenId-authority for AzureAD has the form of <code><span class="col-black">'''<nowiki>https://login.microsoftonline.com/</nowiki><your authority>/'''</span></code> | ||
Remember to save. | Remember to save. | ||
| Line 31: | Line 31: | ||
[[File:2018-05-28 13h34 06.png|none|thumb|594x594px]] | [[File:2018-05-28 13h34 06.png|none|thumb|594x594px]] | ||
[[File:2018-05-28 13h34 52.png|none|thumb|384x384px]] | [[File:2018-05-28 13h34 52.png|none|thumb|384x384px]] | ||
If this was the first login, a new SysUser object was created | If this was the first login, a new SysUser object was created. You are now done with Single Sign On (SSO) via OpenId. | ||
[[Category:MDriven Turnkey]] | [[Category:MDriven Turnkey]] | ||
[[Category:Authentication]] | [[Category:Authentication]] | ||
{{Edited|July|12| | {{Edited|July|12|2025}} | ||
Latest revision as of 05:59, 20 January 2025
You can protect your Turnkey application with your active directory via Azure AD.
1. You should already have a Turnkey web app
2. You should have sufficient rights to register web apps in your organization's Azure AD
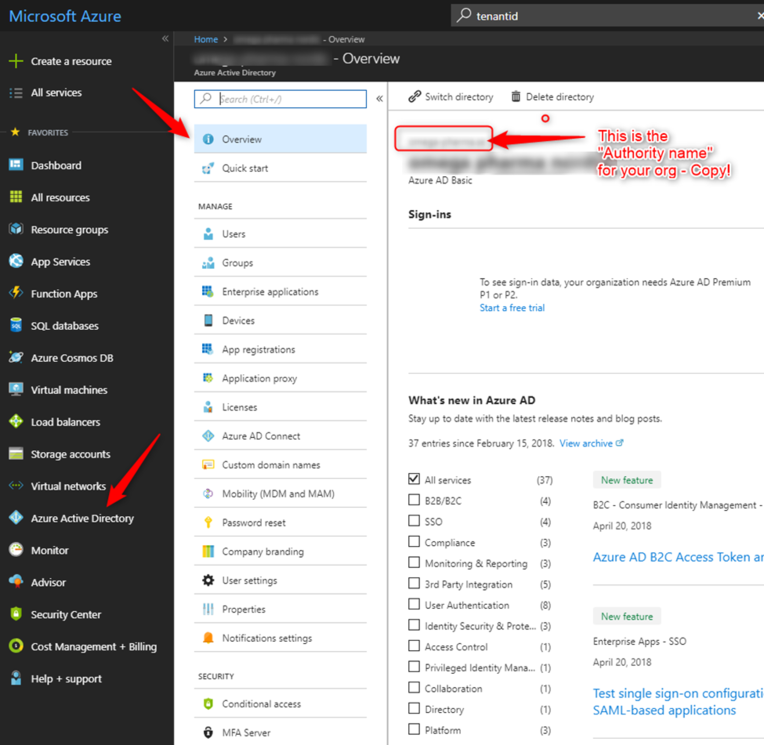
Login into Portal Azure and go to Azure Active Directory:
Make a copy of your AD name (the authority name).
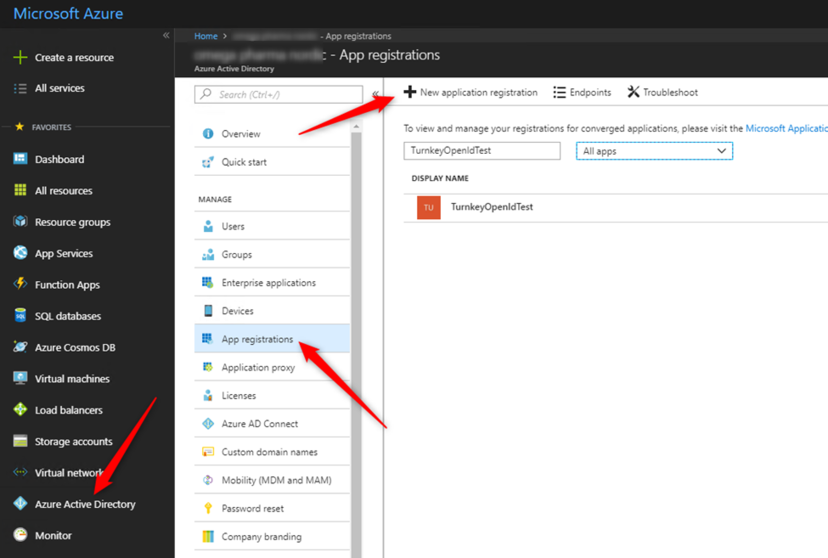
Then App Registrations, New Application registration:
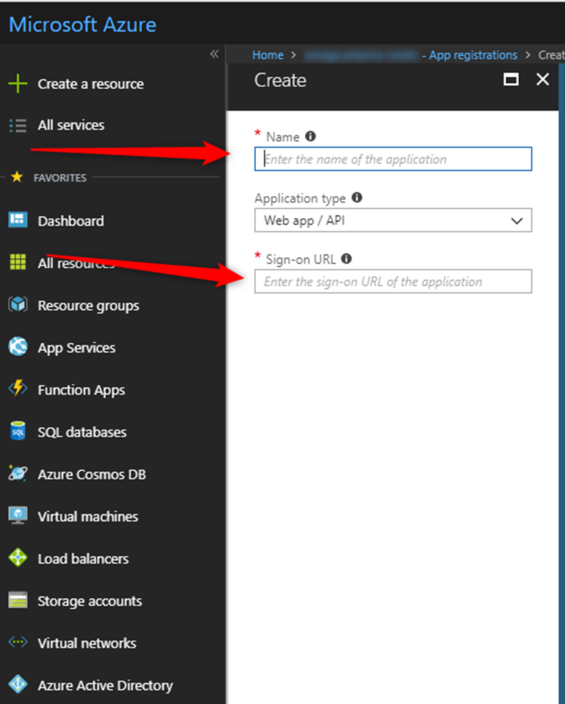
Enter a name for your application (just an easy-read identifier).
Also enter the sign-on URL to your Turnkey – in my case: https://hkscratch.azurewebsites.net/Account/Login
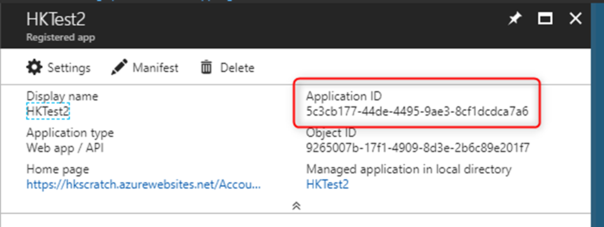
You will get this screen with important information:
Copy the application ID.
You now have the Application ID Guid and the Authority name. We will now assign these to your application via the Turnkey-portal:
Paste your values in – then click on Send Settings And Restart:
The value for OpenId-authority for AzureAD has the form of https://login.microsoftonline.com/<your authority>/
Remember to save.
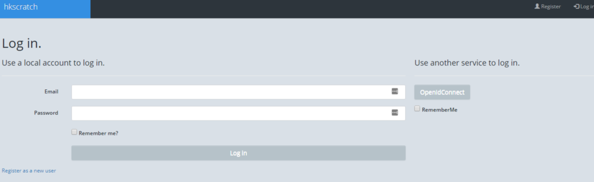
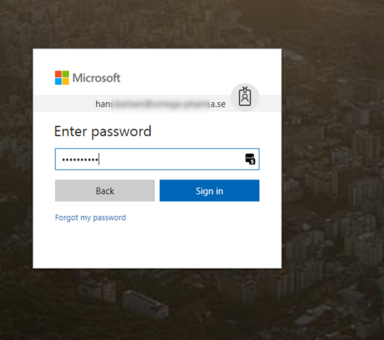
Your application now has an OpenId button and when you click it, you are taken to the OpenId-authority for verification:
If this was the first login, a new SysUser object was created. You are now done with Single Sign On (SSO) via OpenId.